
PowerShell For Pentesters
- 3 minsOverview
This blog covers the principle uses of PowerShell in Penetration Tests. Interacting with files, scanning the network and system enumeration…
Basic PowerShell Commands
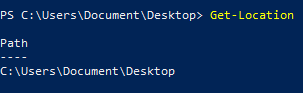
Get the current working directory
Get-Location
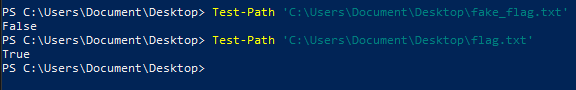
Checking the existence of a path
Test-Path 'C:\Users\Document\Desktop\fake_flag.txt'
Test-Path 'C:\Users\Document\Desktop\flag.txt'
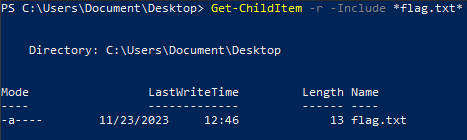
Get the location of a file
Get-ChildItem -r -Include *flag.txt*
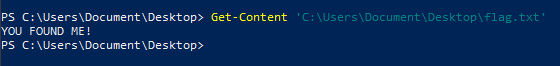
Get the content of a file
Get-Content 'C:\Users\Document\Desktop\flag.txt'
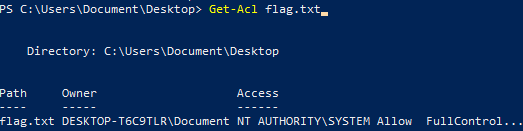
Know the owner of a file
Get-Acl 'C:\Users\Document\Desktop\flag.txt'
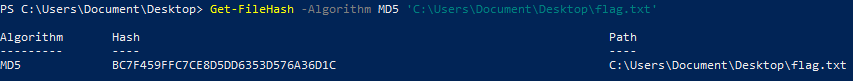
Get the MD5 hash of a file
Get-FileHash -Algorithm MD5 'C:\Users\Document\Desktop\flag.txt'
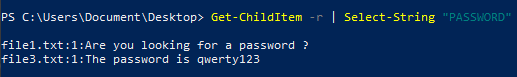
Search for files containing PASSWORD
Get-ChildItem -r | Select-String "PASSWORD"
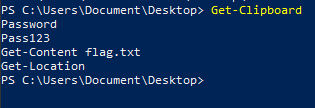
Get Clipboard
Get-Clipboard
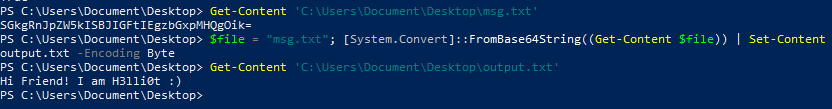
Base64 decoding a file
$file = "msg.txt"; [System.Convert]::FromBase64String((Get-Content $file)) | Set-Content output.txt -Encoding Byte
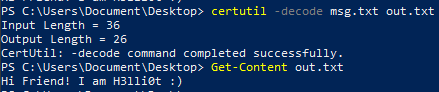
certutil -decode msg.txt out.txt
Secure String to Plaintext
$pw = "<Password>" | convertto-securestring
$cred = new-object system.management.automation.pscredential("H3lli0t", $pw)
$cred.getnetworkcredential() | fl *
Enumeration
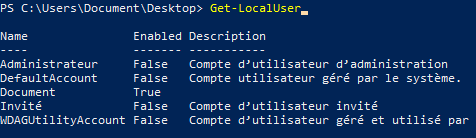
List users on the machine
Get-LocalUser
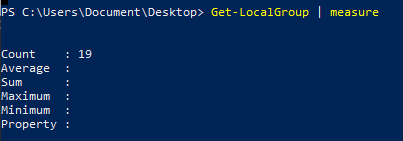
List groups on the machine
Get-LocalGroup | measure
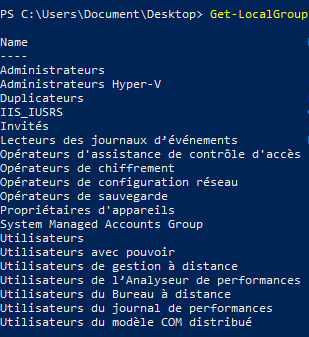
Get-LocalGroup
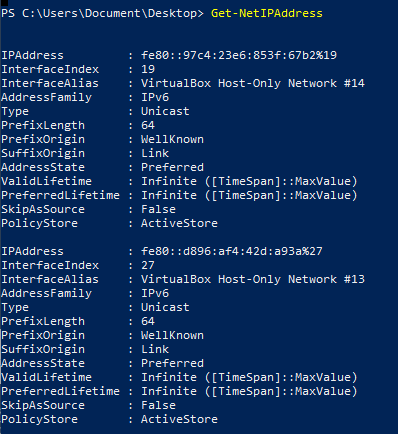
Get IP address info
Get-NetIPAddress
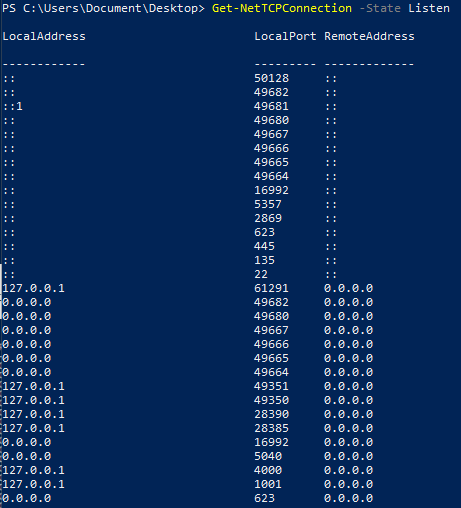
List listening connections
Get-NetTCPConnection -State Listen
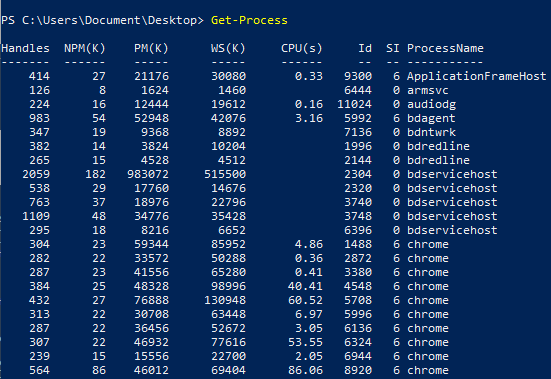
List running processes
Get-Process
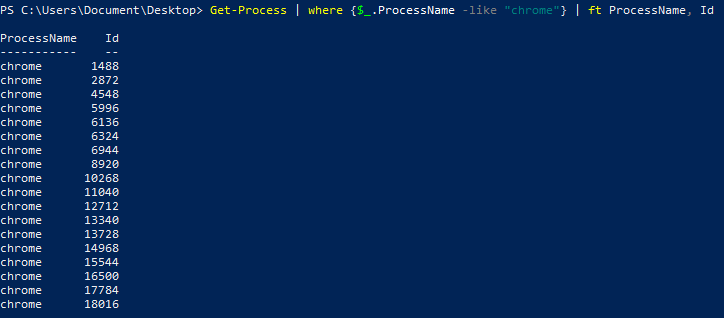
Get-Process | where {$_.ProcessName -like "chrome"} | ft ProcessName, Id
Get running services
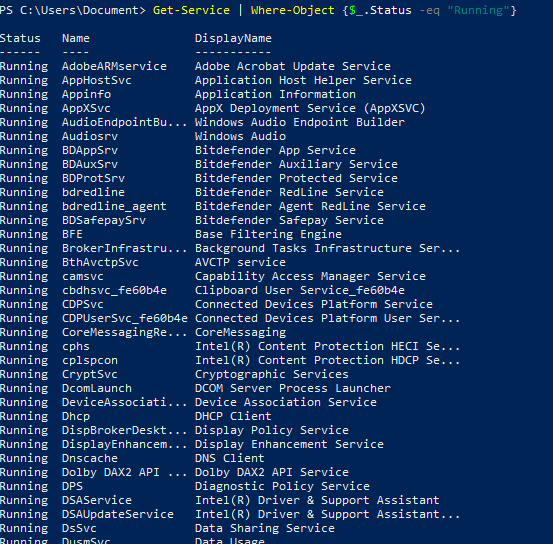
Get-Service | Where-Object {$_.Status -eq "Running"}
Get scheduled tasks
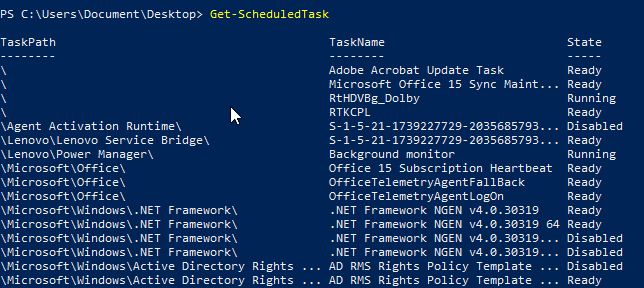
Get-ScheduledTask
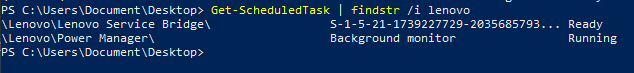
Get-ScheduledTask | findstr /i lenovo
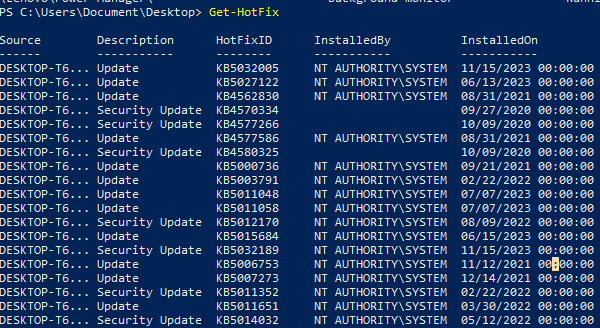
List applied patches
Get-HotFix
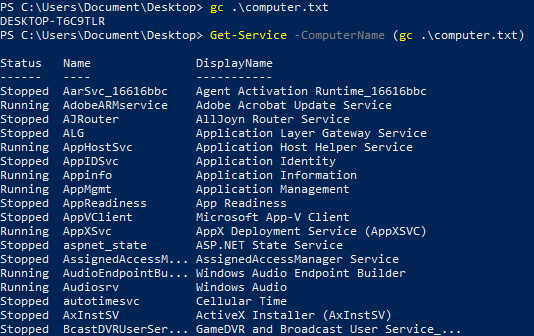
Multiple-Value Parameters
Get-Service -ComputerName (gc .\computer.txt)
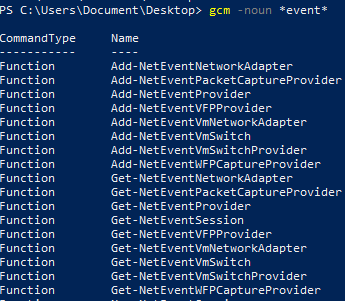
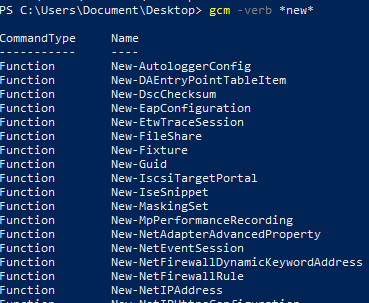
Using Get-Command
gcm -noun *event*
gcm -verb *new*
List available modules
Get-Module -ListAvailable
Summary
PowerShell proves to be an indispensable tool for penetration testers, offering a powerful platform to assess and enhance the security of systems. Its scripting capabilities, coupled with a wide range of built-in functions, enable testers to automate tasks and exploit vulnerabilities. That’s what makes Powershell a key component in a pentester’s toolkit.
That was the end of the blog, thanks for reading, I hope you learnt something new.
Happy Hacking!
