CMD For Pentesters
- 2 minsOverview
This blog covers the principle commands in windows used in different stages of a penetration test like system enumeration, domain recon, post exploitation…
Basic Windows Commands
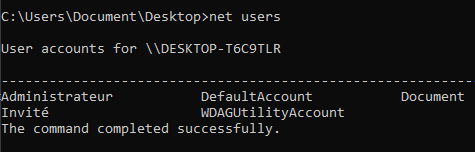
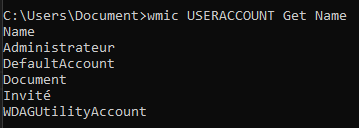
List all users
net users
wmic USERACCOUNT Get Name
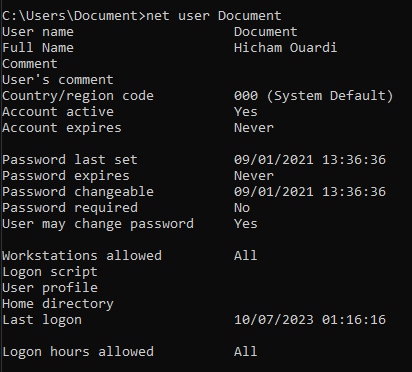
Get user info
net user %username%
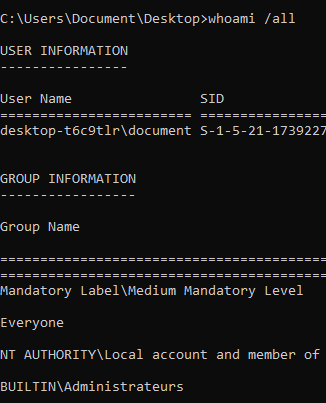
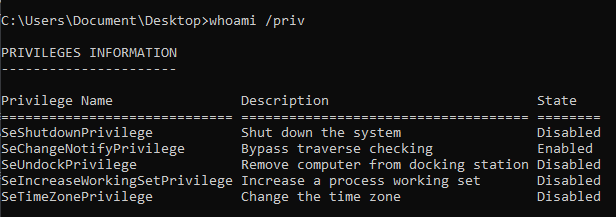
Get the current user & privilege info
whoami /all
whoami /priv
Create user
net user /add [username] [password]
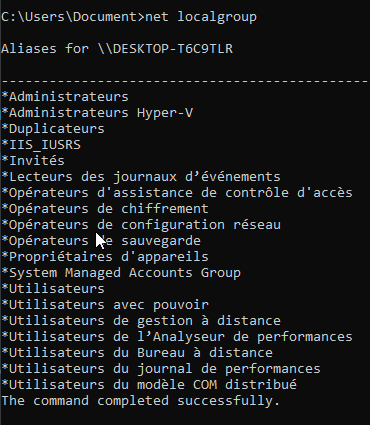
List all groups
net localgroup
Add user to a group
net localgroup [groupname] [username] /add
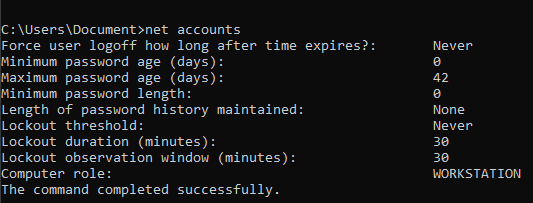
List password requirements info
net accounts
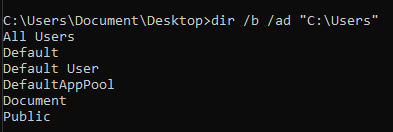
List content of a directory
dir /b /ad "C:\\Users"
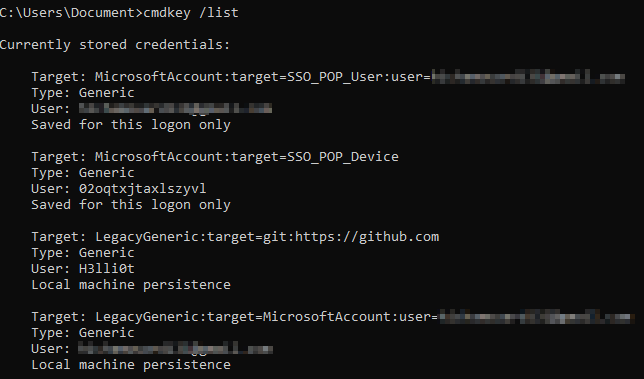
List stored credentials
cmdkey /list
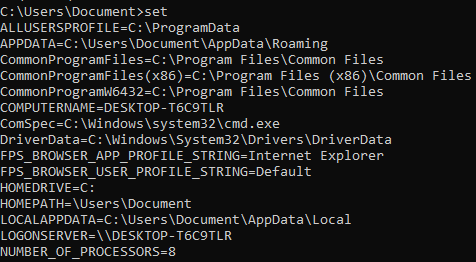
List all environment variables
set
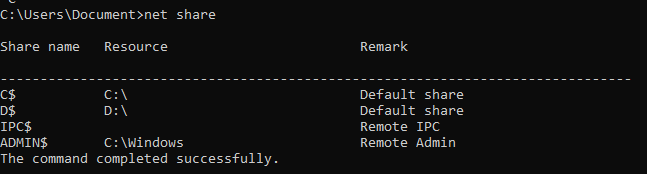
View current network shares
net share
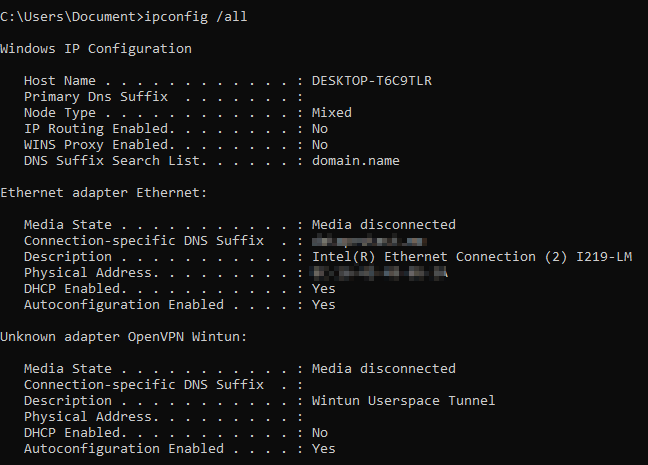
View info about interfaces
ipconfig /all
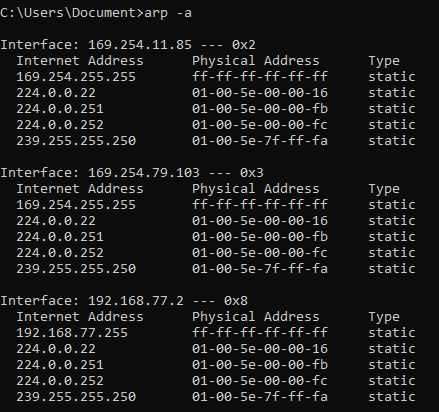
Print known hosts
arp -a
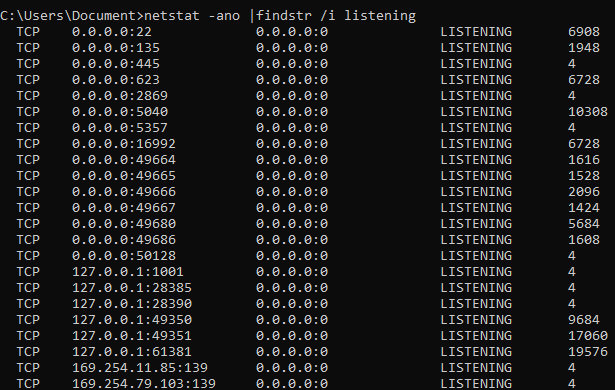
List open ports
netstat -ano | findstr /i listening
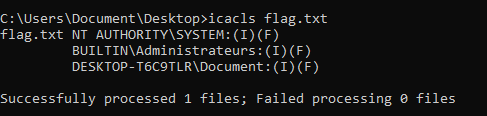
Get file permissions
icacls flag.txt
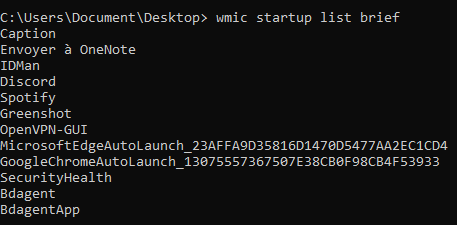
List startup programs
wmic startup list brief
List running services
sc query type=service
Summary
Every penetration tester should be fluent with the Windows command prompt since various commands could be used in different stages of a penetration test like domain recon and post exploitation. That’s why being fluent in CMD is a must for pentesters.
That was the end of the blog, thanks for reading, I hope you learnt something new.
Happy Hacking!
